京麒ctf 2025热身赛re wp

re1
puts密文后爆破就行

1 | from string import printable |
re2
实际只有一个异或,异或结果和输入前两位有关系
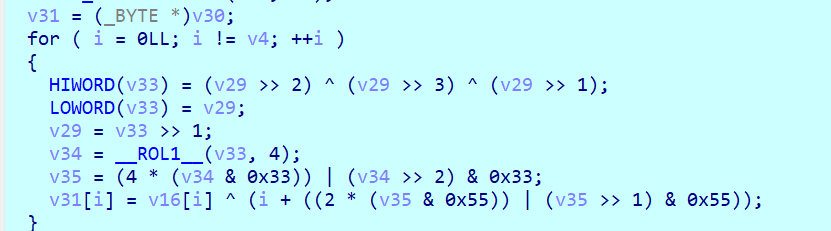
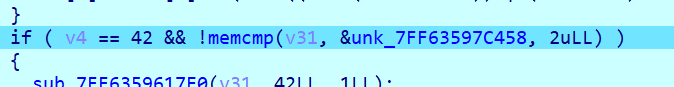
直接爆前2位就行了
1 | import subprocess |
显然得到前两位是fl
输入”fl”+”0”*40,然后拿到异或的结果与密文,就能异或得到flag
1 | key="fl"+"0"*40 |
1 | #搓算法像个糖批 |
- Title: 京麒ctf 2025热身赛re wp
- Author: clev1L
- Created at : 2025-04-23 11:18:55
- Updated at : 2025-04-23 11:36:55
- Link: https://github.com/clev1l/2025/04/23/jqctf-2025热身赛re-wp/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments