UCSCCTF2025 WP

simplere-ucsc
脱壳,发现脱不掉
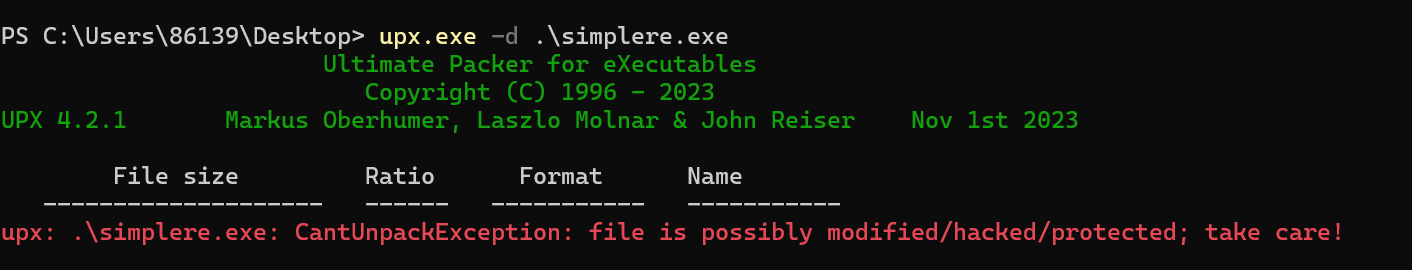
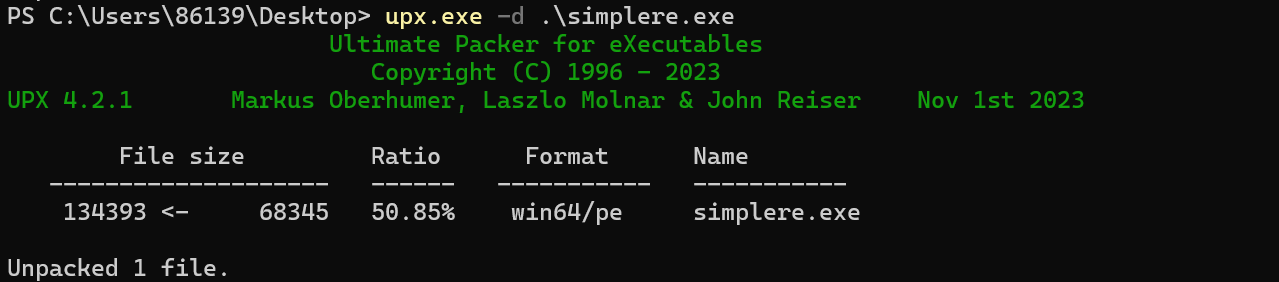
010打开修一下特征码
ida64打开,看到两个加密obfuscate_encode和obfuscate_transpose_xor
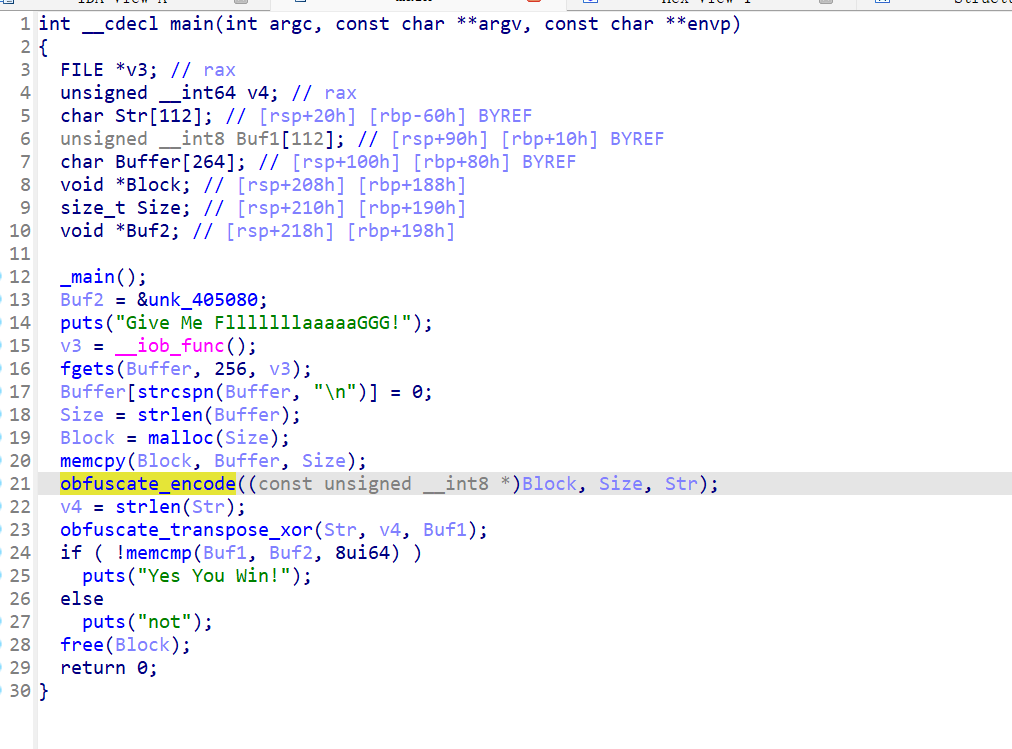
obfuscate_encode可以看出是换表base58,表是wmGbyFp7WeLh2XixZUYsS5cVv1ABRrujdzQ4Kfa6gP8HJN3nTCktqEDo9M
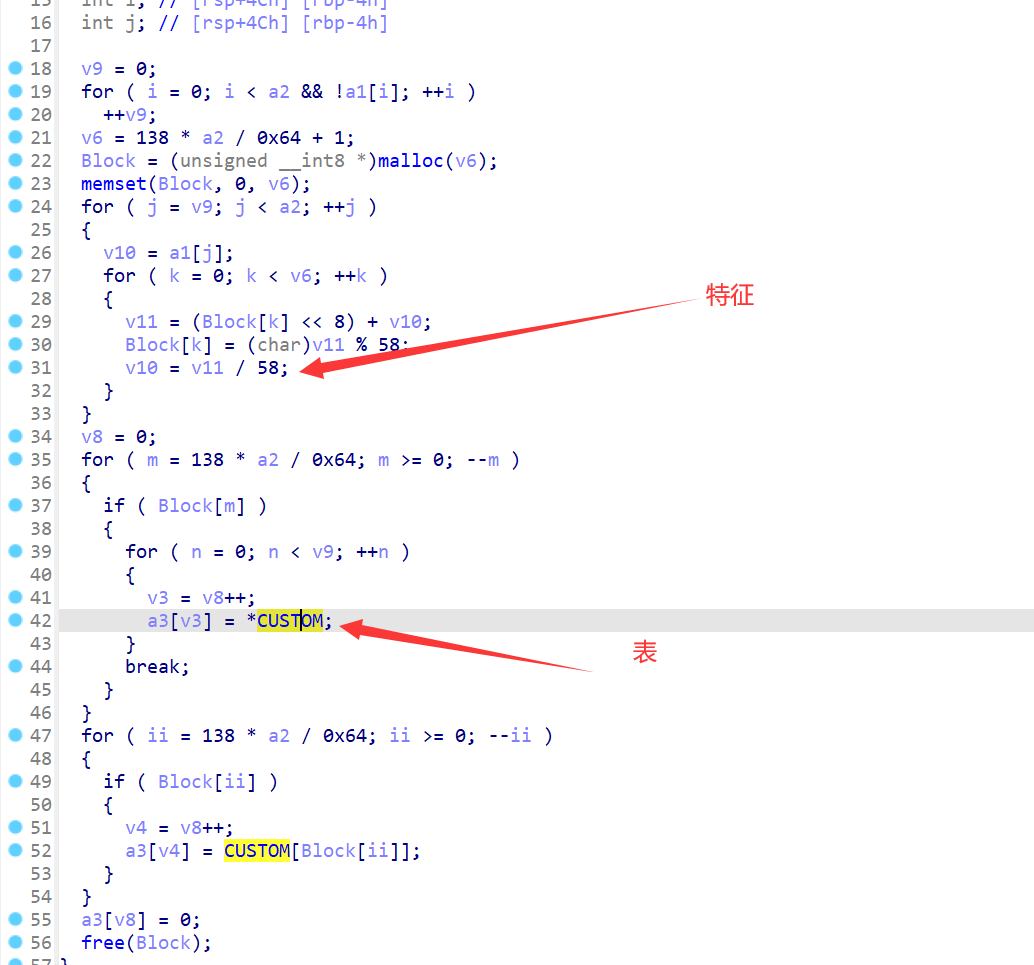
obfuscate_transpose_xor就是个简单的异或
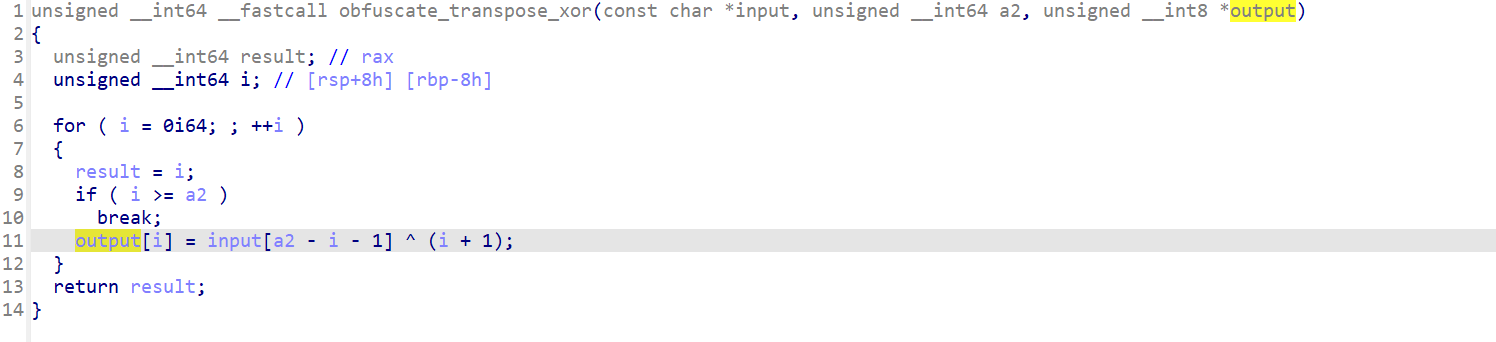
很显然,input[a2 - i - 1] = output[i] ^ (i + 1);
1 | data=[0x72, 0x7A, 0x32, 0x48, 0x34, 0x4E, 0x3F, 0x3A, 0x42, 0x33, |
再解base得到flag
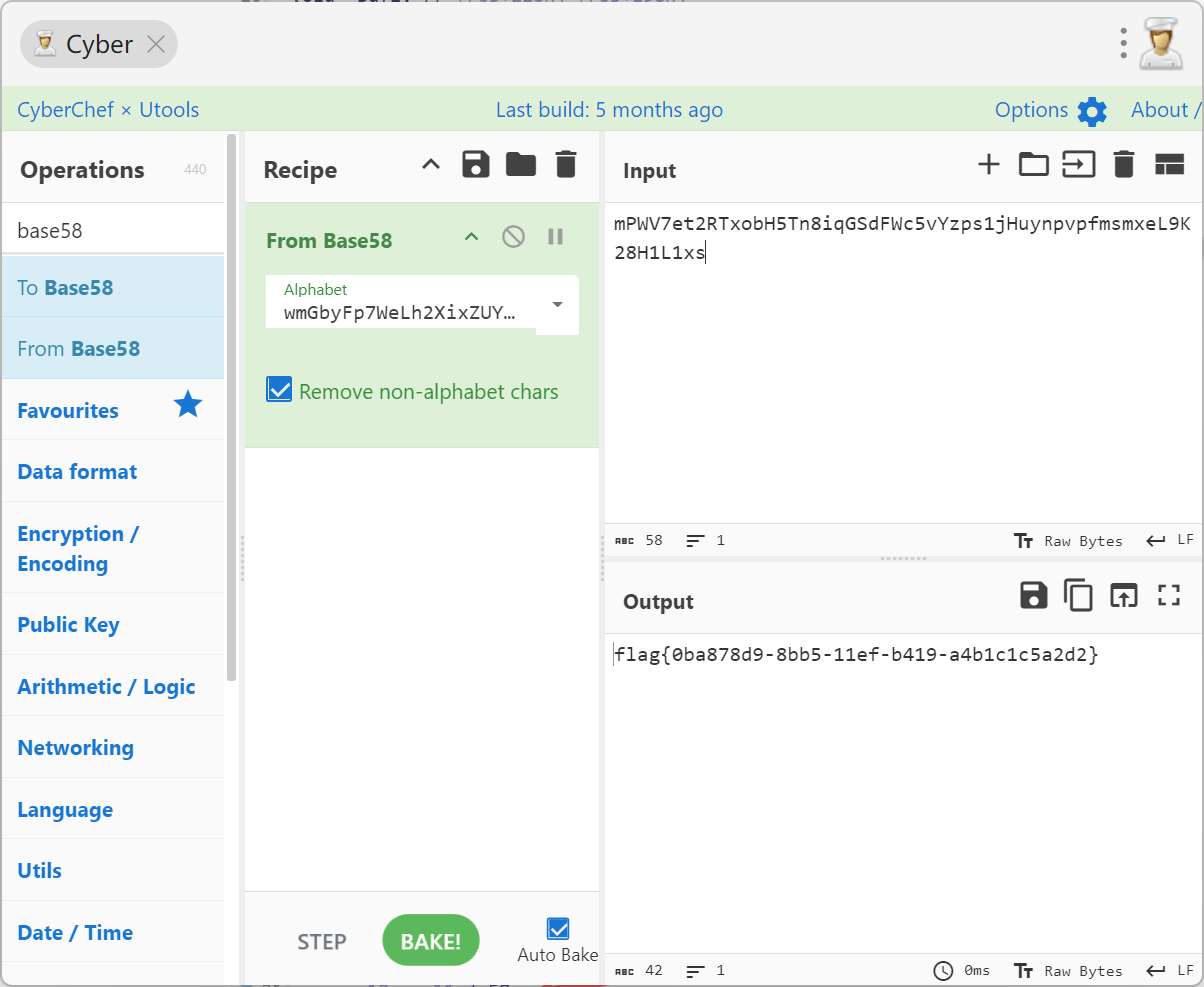
flag{0ba878d9-8bb5-11ef-b419-a4b1c1c5a2d2}
easy_re-ucsc
ida64打开
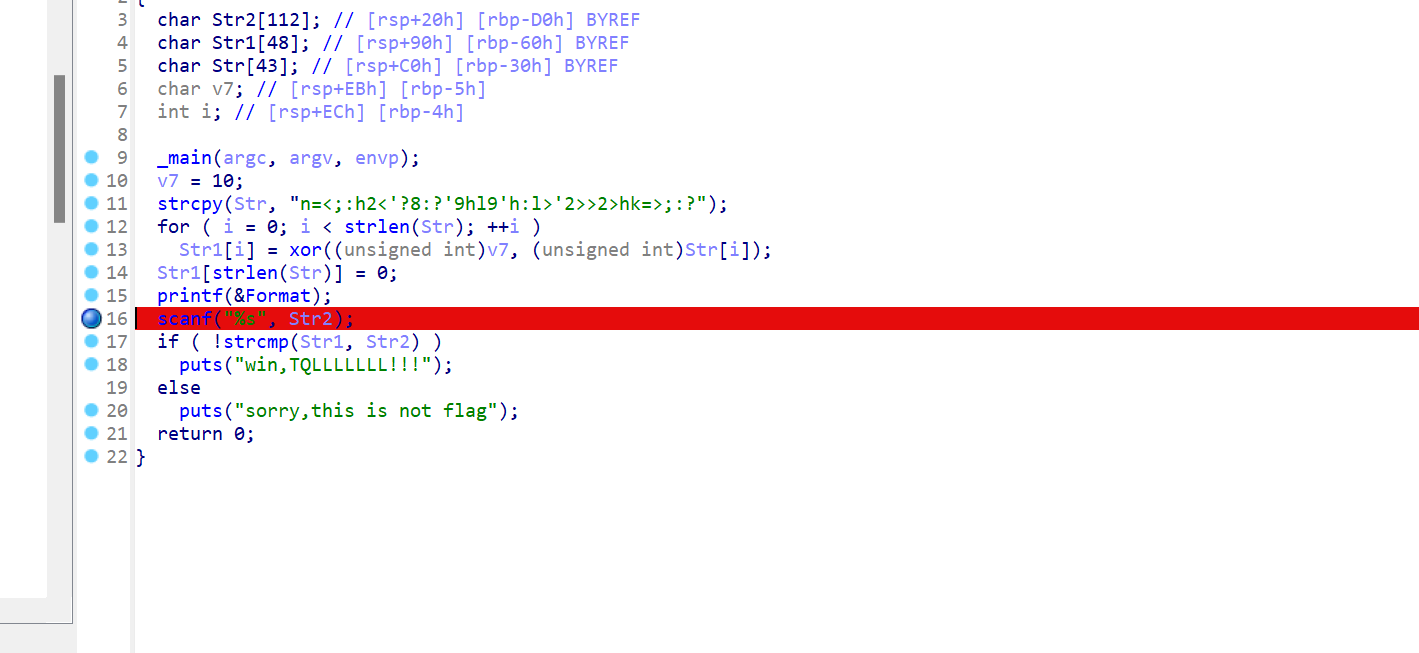
断在这,直接动调,拿str1就是flag
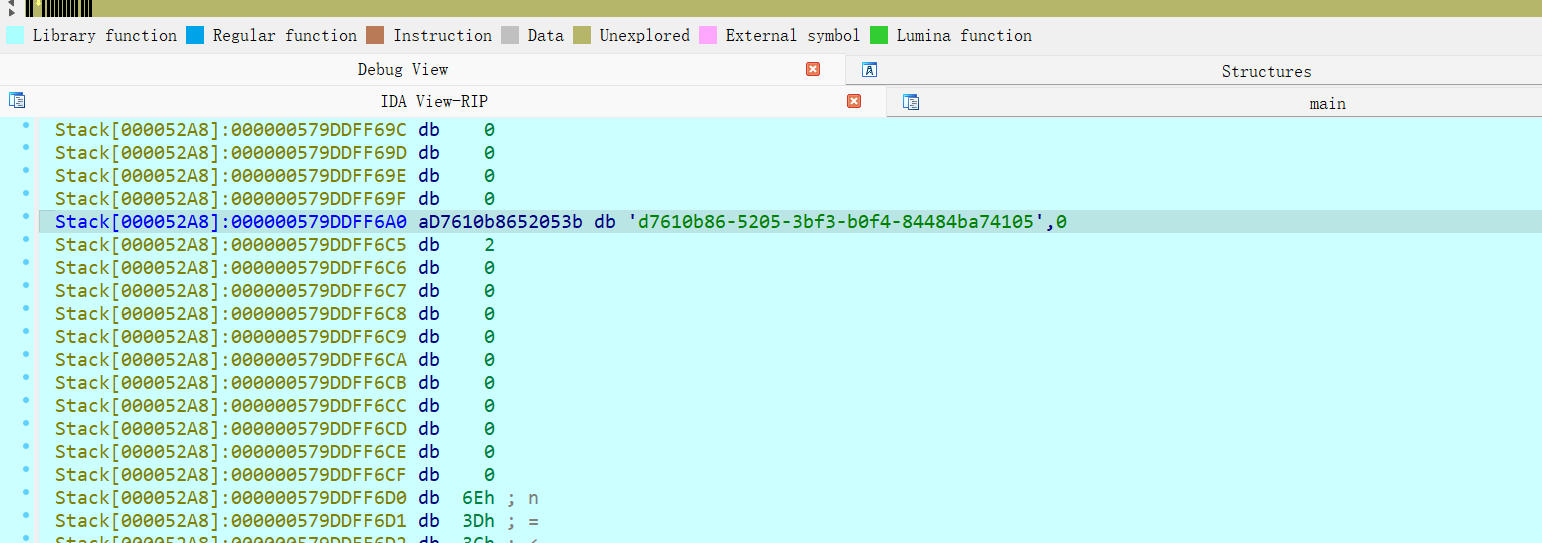
flag{d7610b86-5205-3bf3-b0f4-84484ba74105}
EZ_debug-ucsc
ida64打开
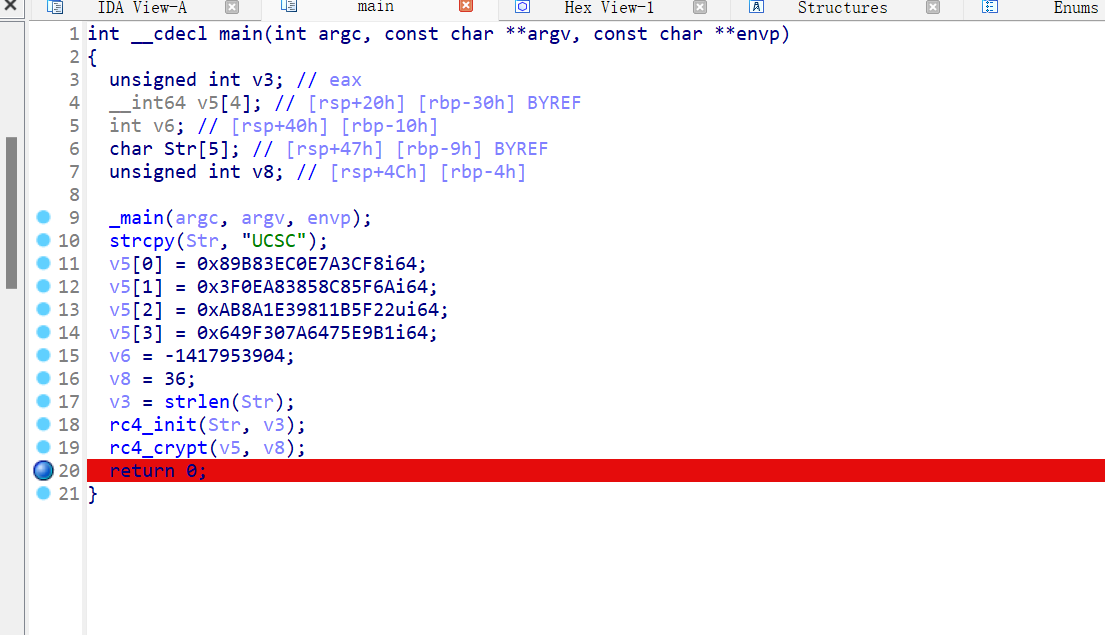
断在这,动调,v5就是flag

flag{709e9bdd-0858-9750-8c37-9b135b31f16d}
re_ez-ucsc
ida9.0打开
动调简单分析一下逻辑
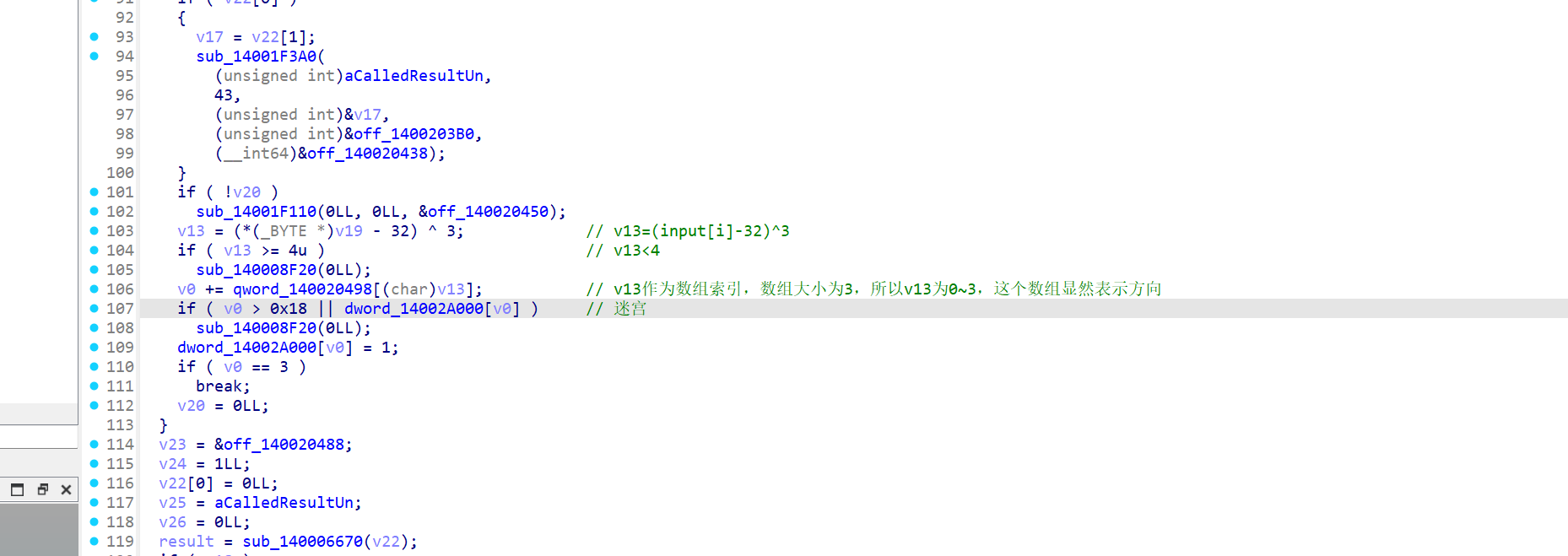
迷宫不大,手动走一下迷宫,然后md5
1 | maps=[0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x00000001, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x00000001, 0x00000001, 0x00000000, 0x00000001, 0x00000000, 0x00000001, 0x00000001, 0x00000000, 0x00000000, 0x00000000, 0x00000001, 0x00000001, 0x00000001, 0x00000001, 0x00000001, 0x00000001] |
- Title: UCSCCTF2025 WP
- Author: clev1L
- Created at : 2025-04-20 21:30:47
- Updated at : 2025-04-20 21:32:46
- Link: https://github.com/clev1l/2025/04/20/UCSCCTF2025-WP/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments