reversing.kr WP

糖题
EasyCrack
拼接字符串拿到flag
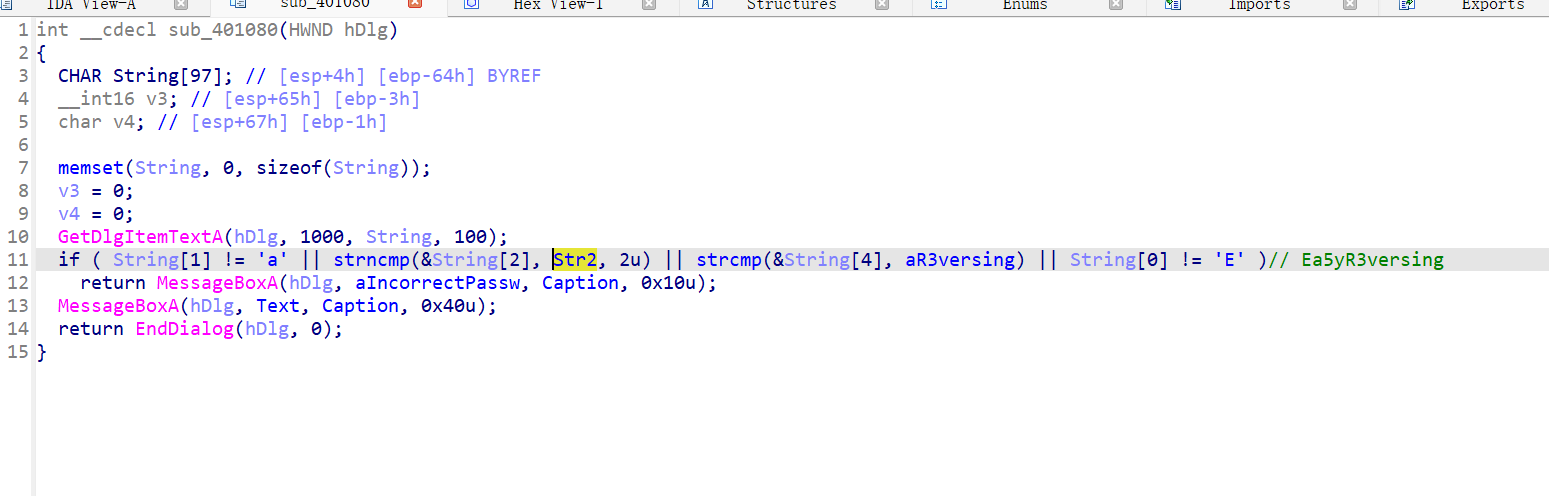
EasyKeygen
动调拿到密钥,加密就一个异或
1 | key=[0x10, 0x20, 0x30] |
Easy Unpack
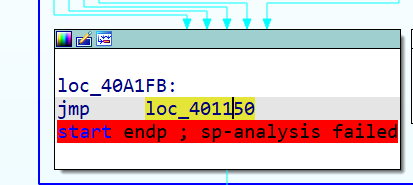
找到大跳转,显然oep为00401150
Replace
假如我们输入0
动调到
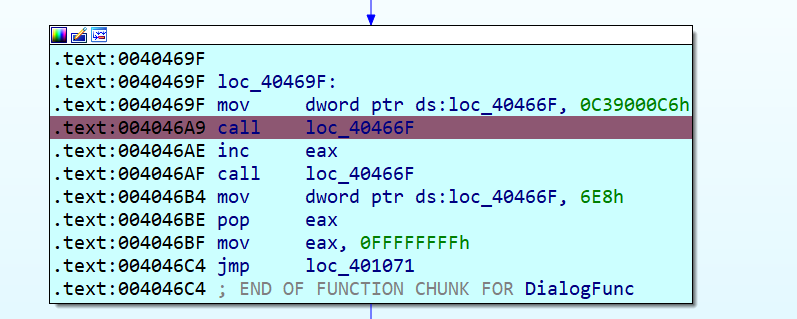
动调看到,对eax除地址进行了nop操作
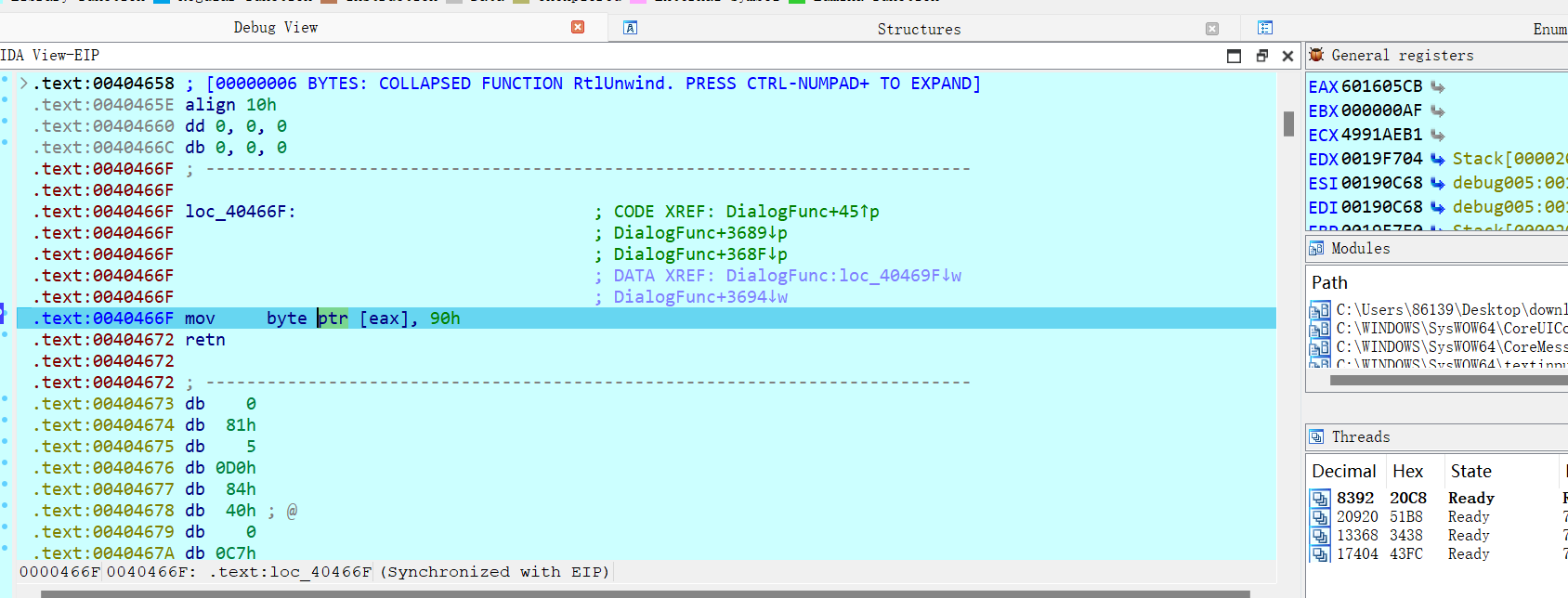
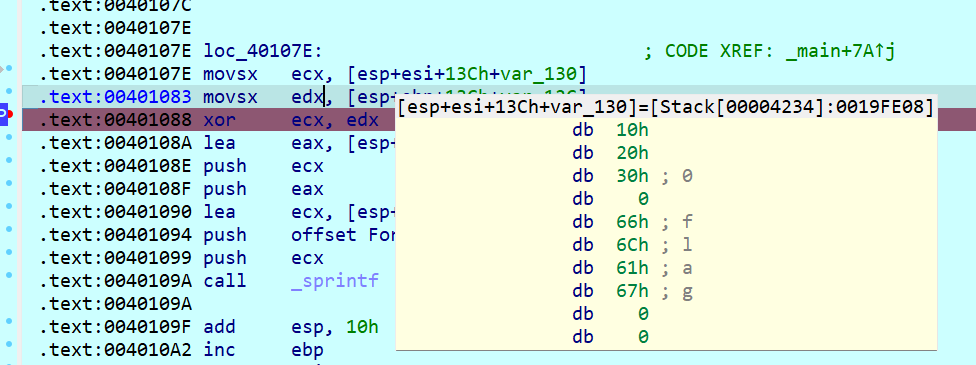
其中eax和输入有关,动调前面知道全是add操作,所以eax=input+0x601605CB
分析外层逻辑,要到correct,可以将0x00401071除代码nop掉即可,所以要保证eax=0x0401071
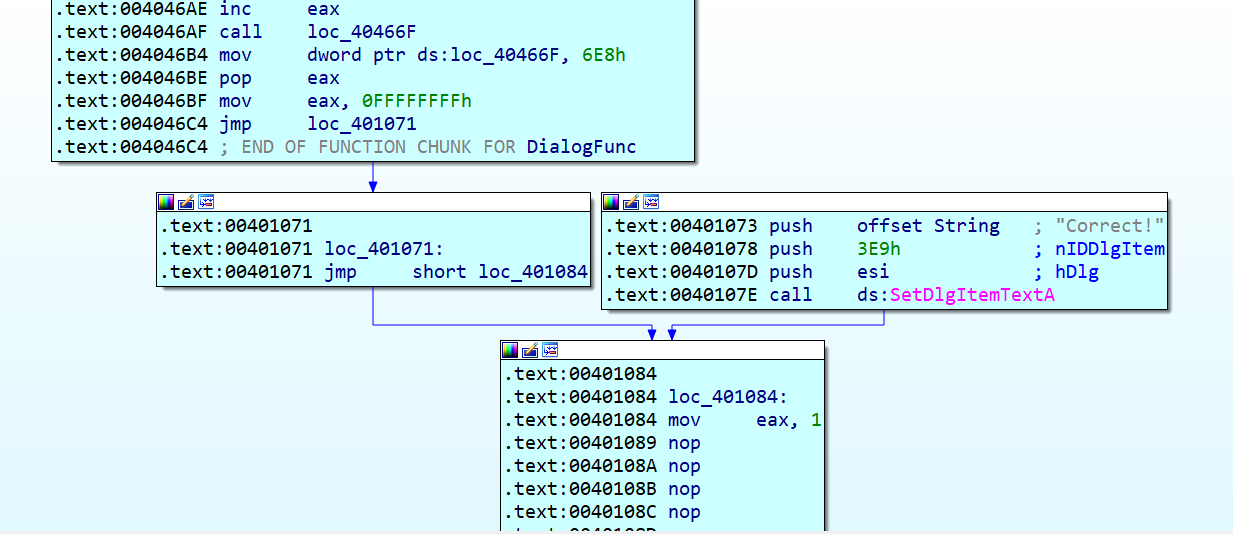
两个操作数对应两个nop
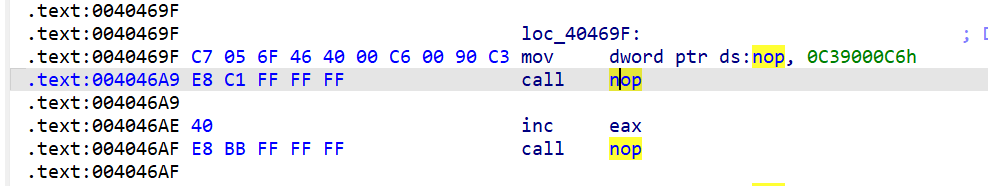

所以得到
1 | print((0x0401071-0x601605CB)&0xffffffff) |
ImagePrc
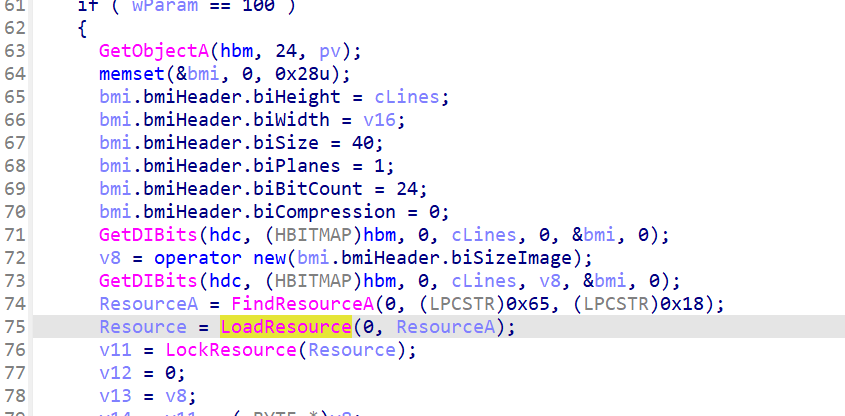
看到LoadResource,用Resourcehacker拿到资源文件
看到数据中基本是大部分ff,小部分0,
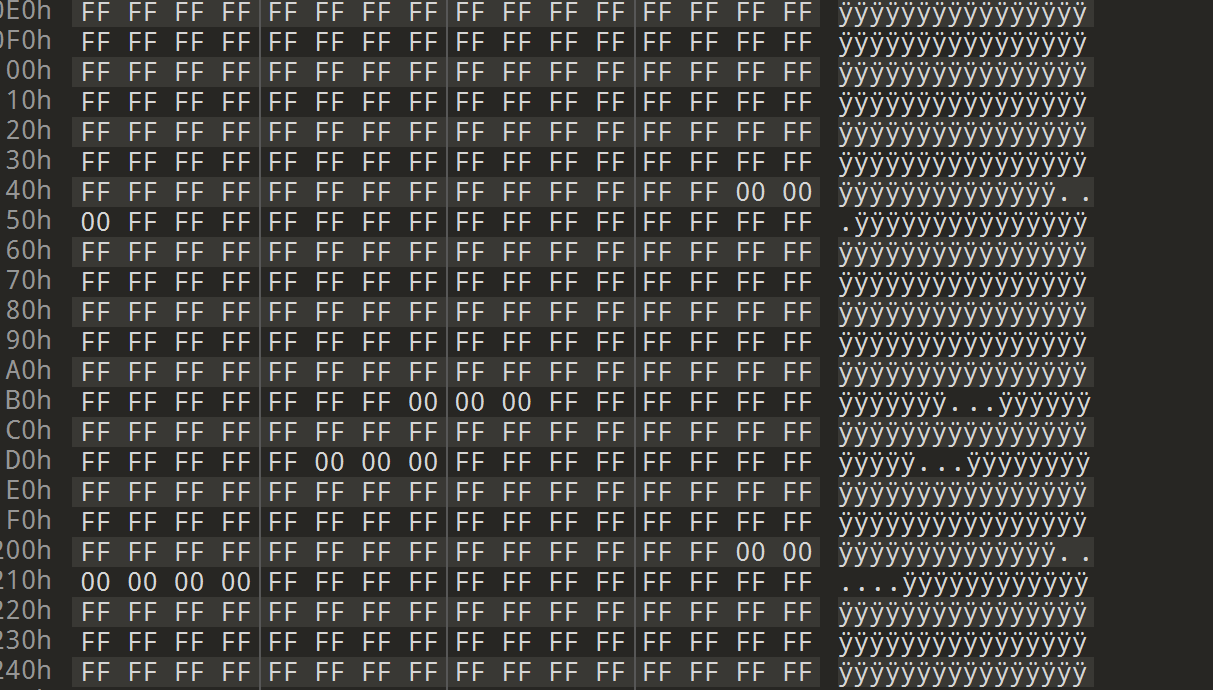
让gpt写个脚本
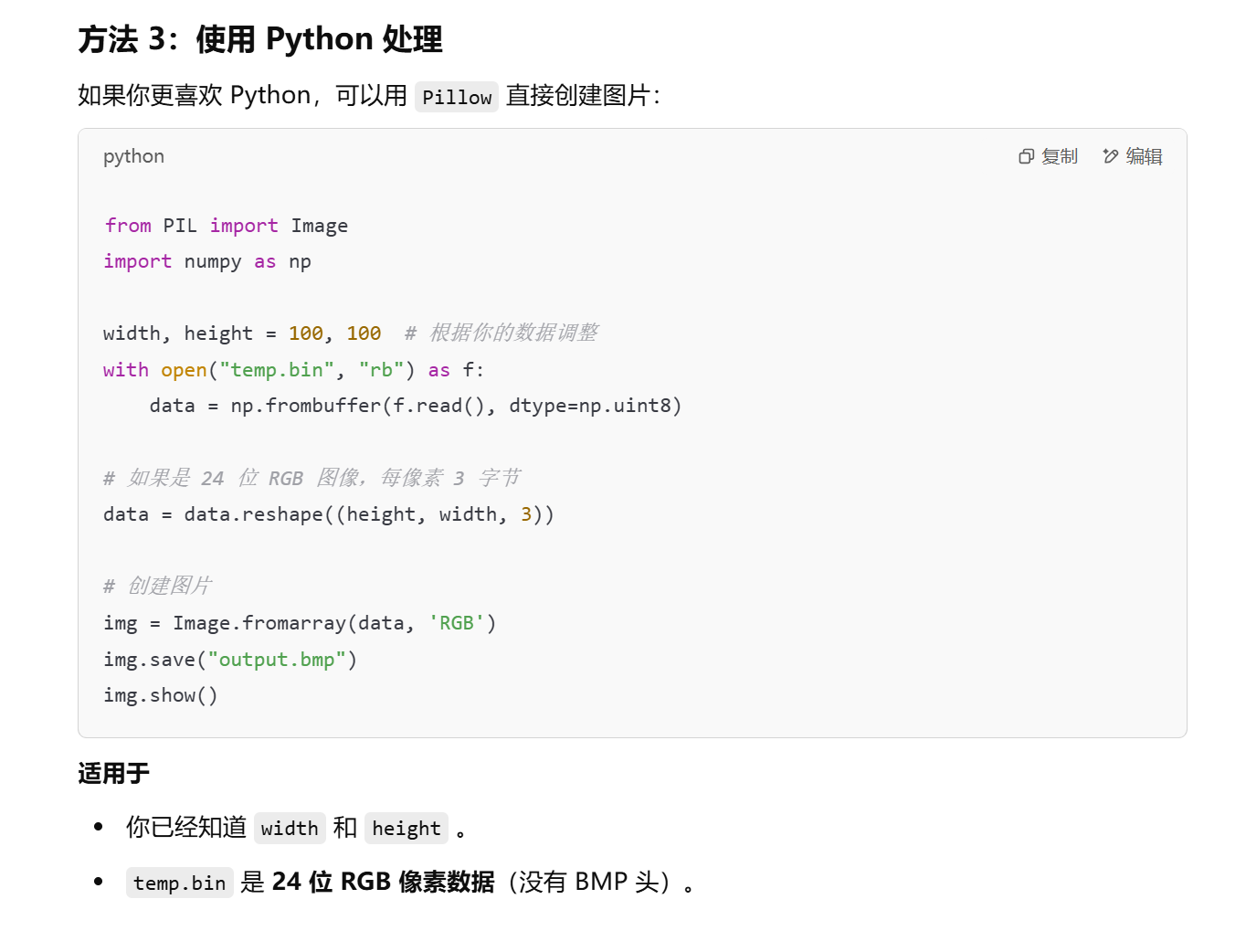
1 | from PIL import Image |
不知道为啥镜像了,但是能看出是GOT
Position
逻辑很显然,直接爆破
1 | for i in range(97, 128): |
EasyELF
异或
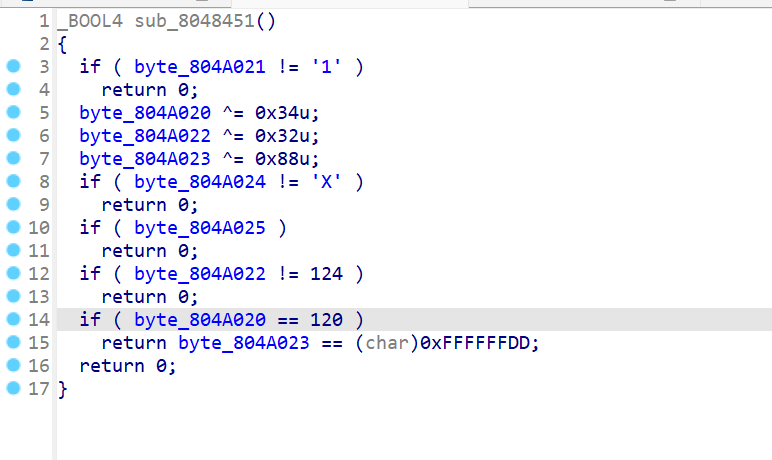
1 | print(chr(0x34^120),"1",chr(0x32^124),chr(0x88^0xdd),"X",sep="") |
Ransomware
脱壳
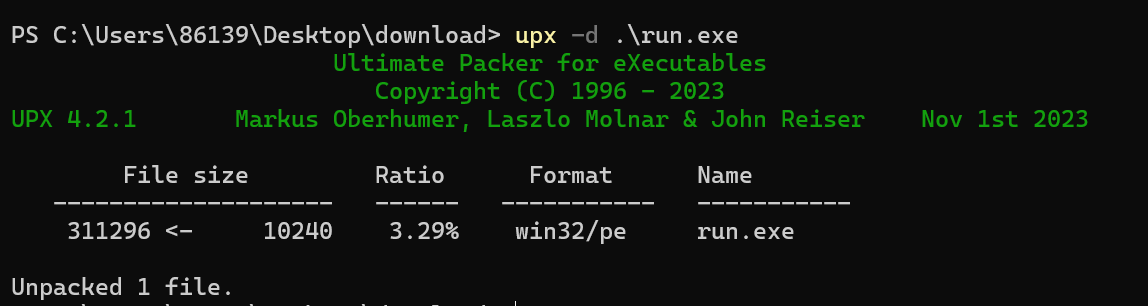
jmp跳过垃圾代码
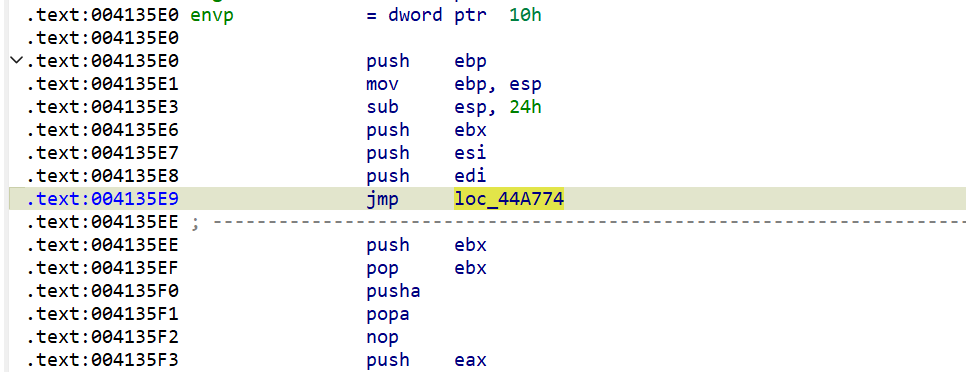
包括401000处的代码也全是垃圾代码,将call 0x401000也全部nop掉,得到加密
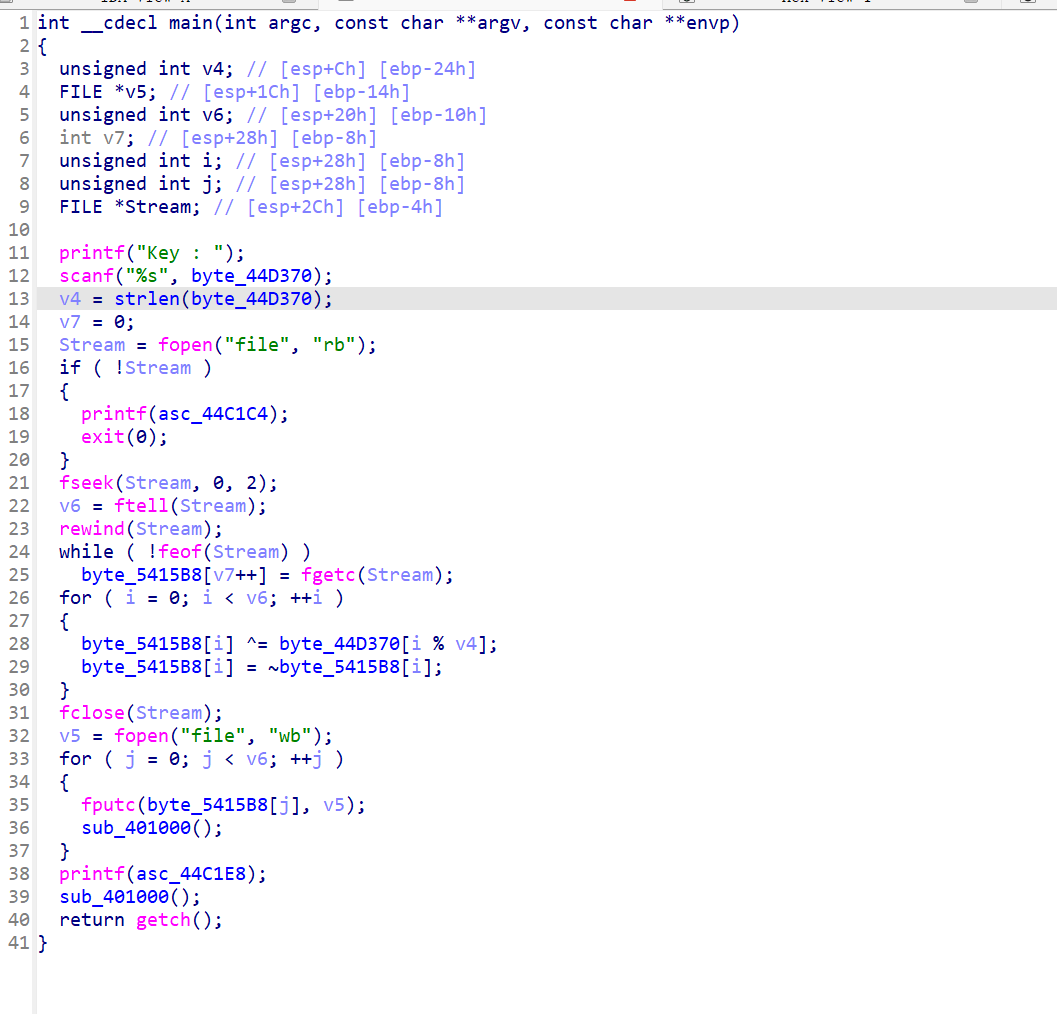
得猜key,但是不知道file是啥文件,猜测是exe,找个exe取头部,与密文解密出key
1 | enc=list(bytes.fromhex("DE C0 1B 8C 8C 93 9E 86 98 97 9A 8C 73 6C 9A 8B")) |
所以key为letsplaychess
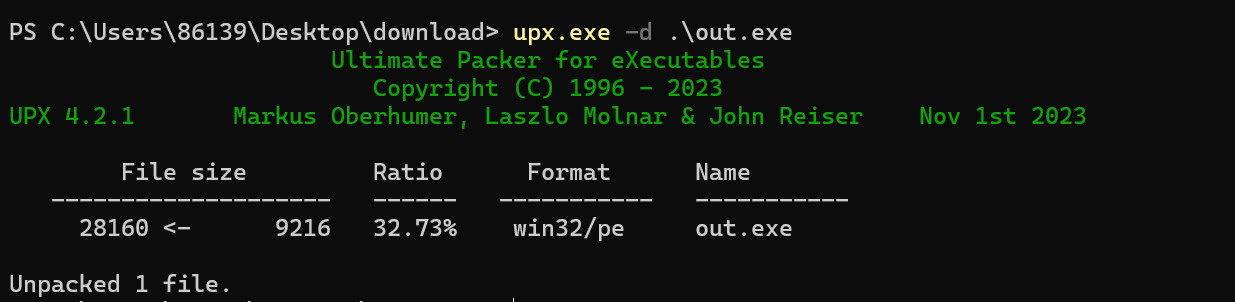
解密file,脱壳
1 | key=[ord(i) for i in "letsplaychess"] |
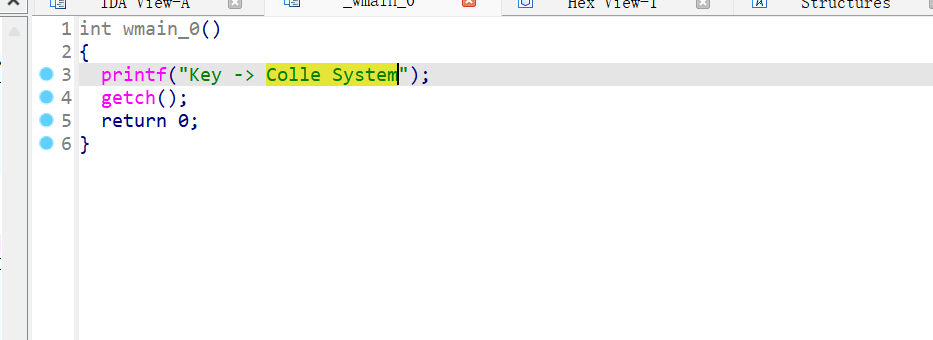
CSHOP
net逆向,dnspy打开
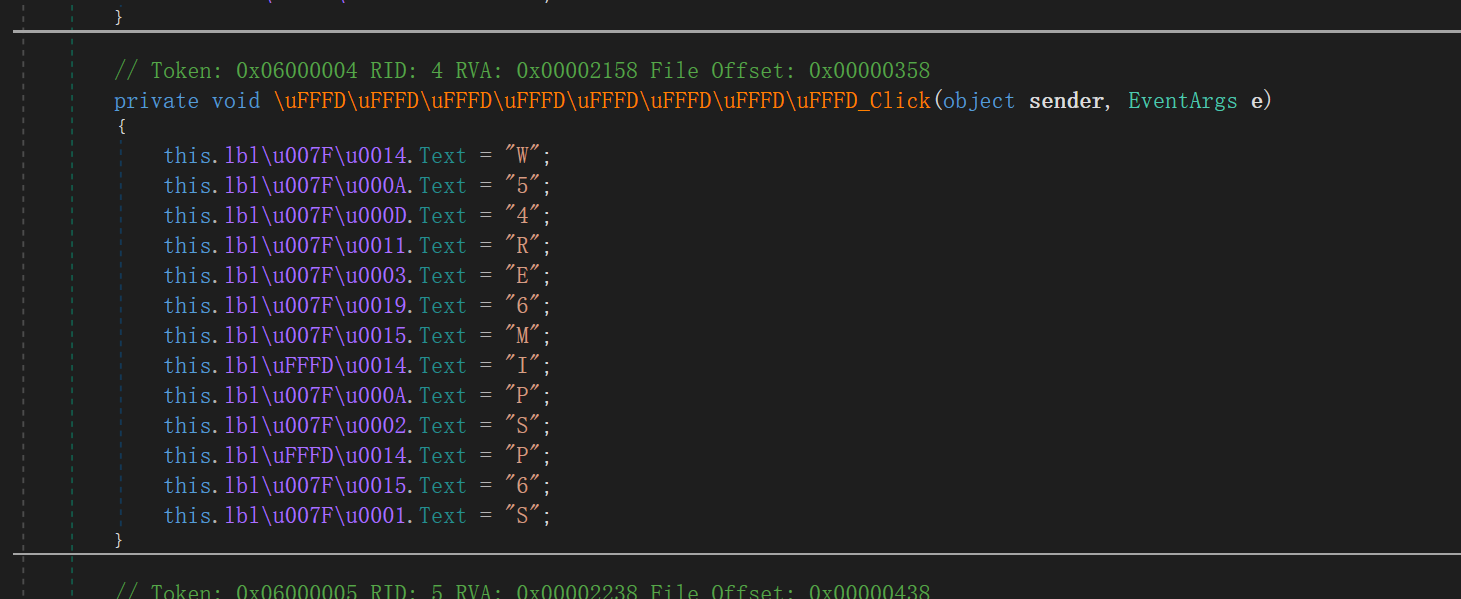
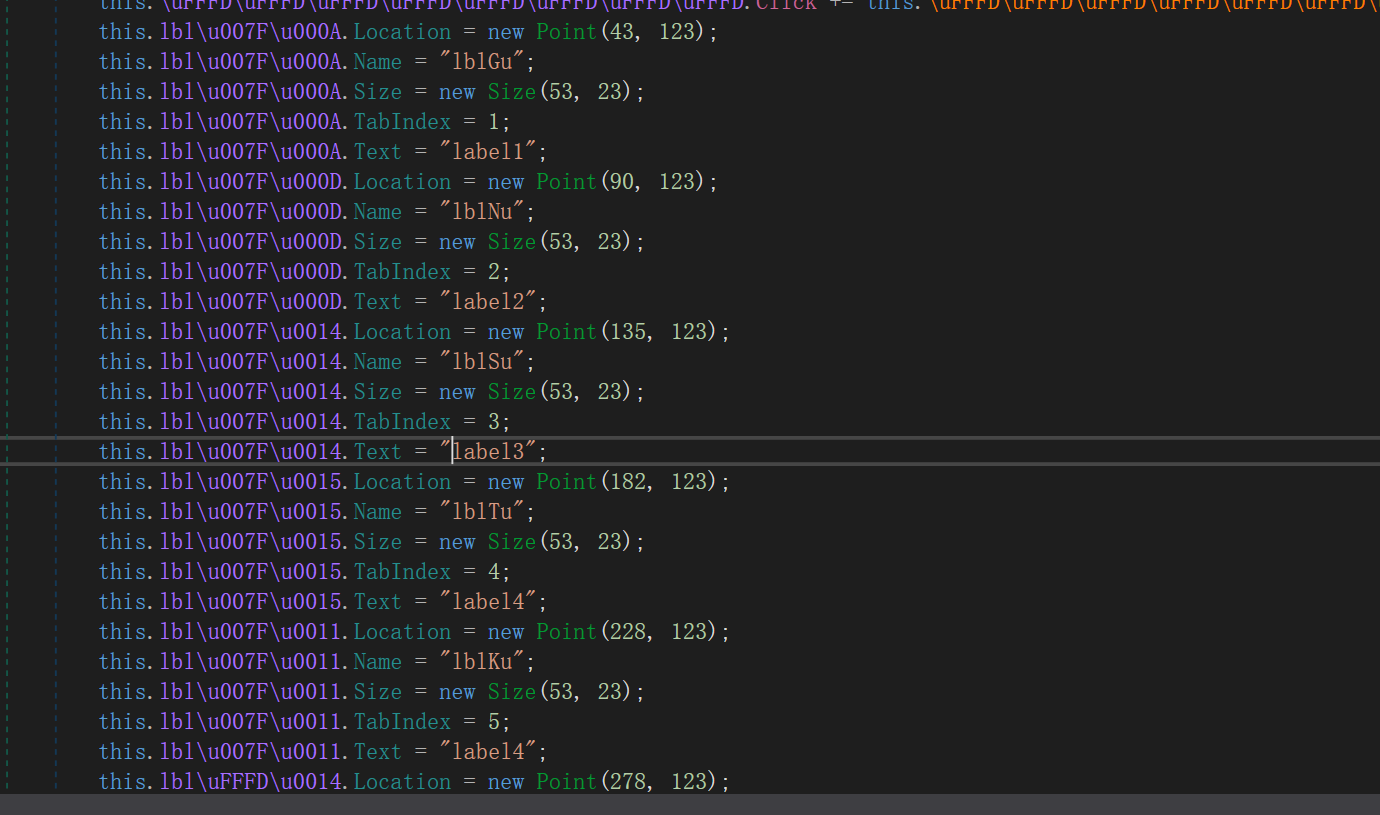
给了标签的位置和字符
根据位置排序一下就行了
1 | t=r''' |
Direct3D_FPS
字符串定位关键代码
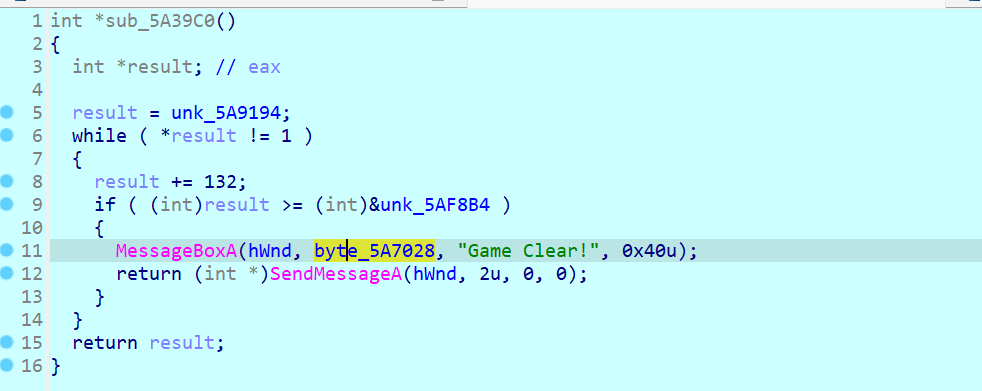
byte_5A7028显然被加密了,交叉引用查看调用
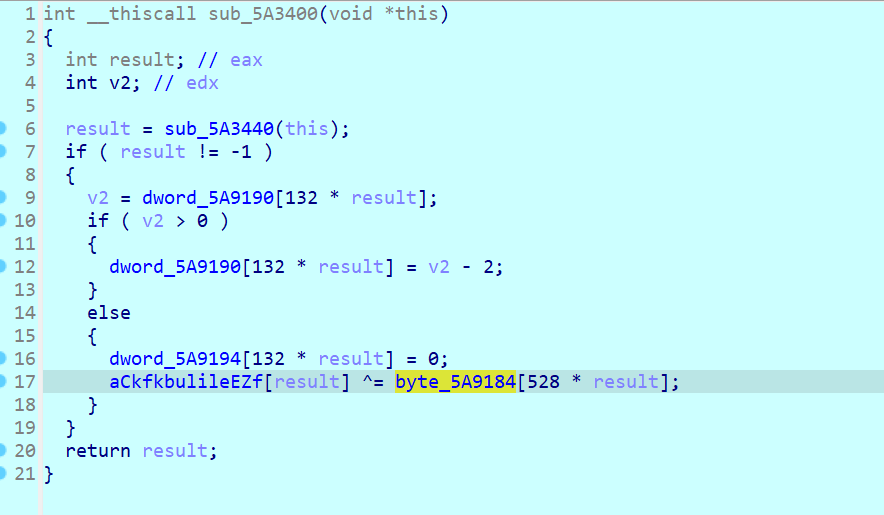
运行起来后idapython获取数据
1 | import ida_bytes |
异或拿到输出
1 | enc=[0x43, 0x6B, 0x66, 0x6B, 0x62, 0x75, 0x6C, 0x69, 0x4C, 0x45, |
Multiplicative
recaf反编译代码
有限域内乘法,求逆元,解密
1 | import gmpy2 |
Music Player
ida中找到检查点
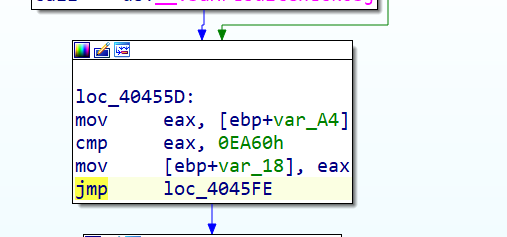
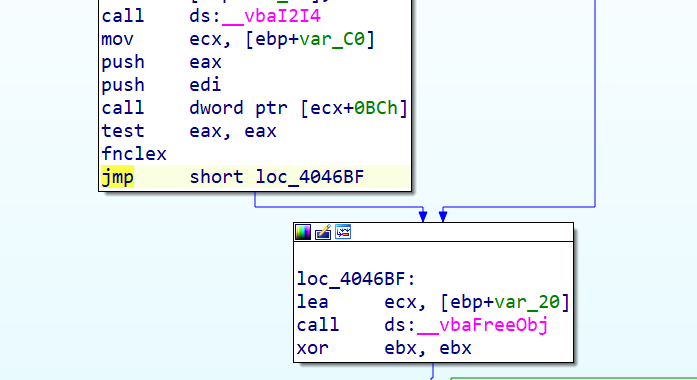
全部改成jmp跳过
AutoHotkey1
脱壳
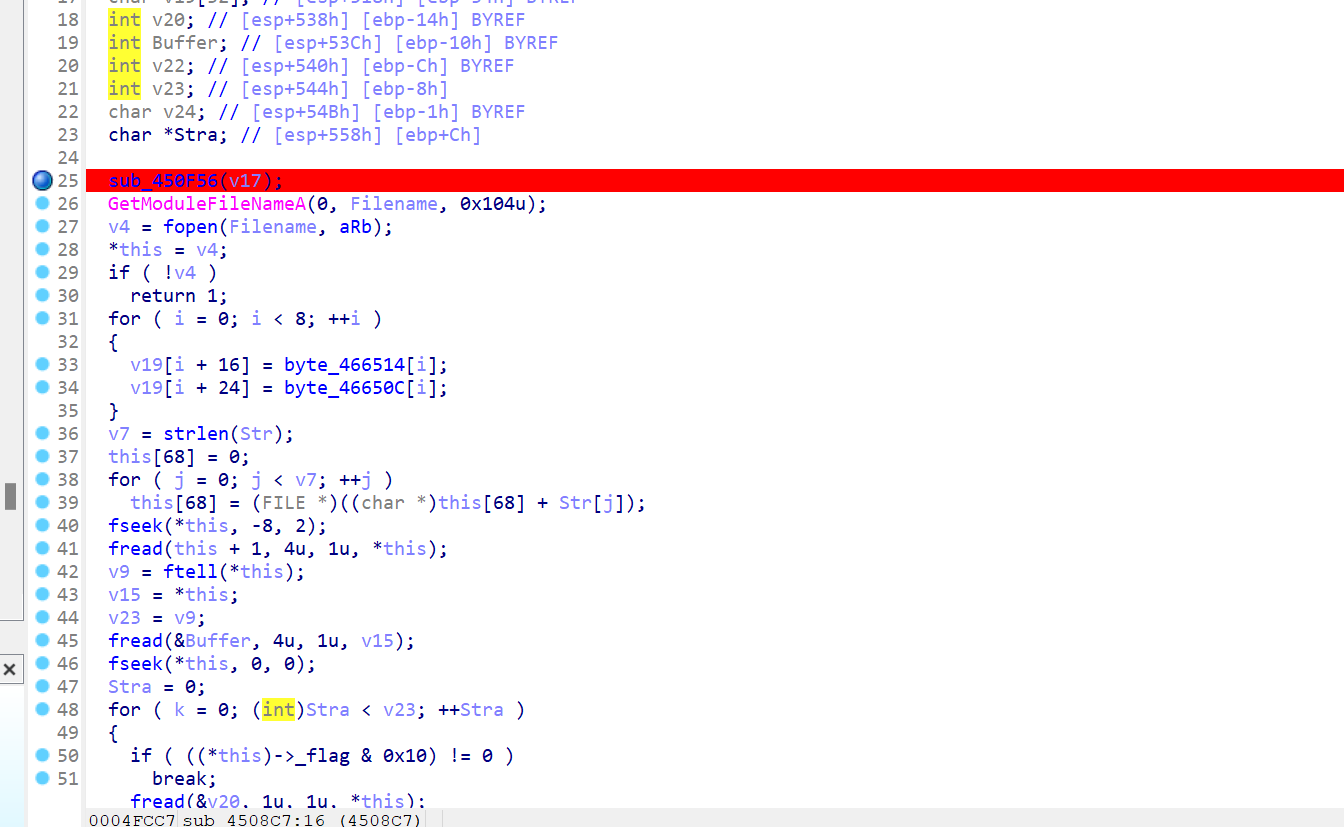
字符串定位关键代码
- Title: reversing.kr WP
- Author: clev1L
- Created at : 2025-02-23 18:28:01
- Updated at : 2025-04-07 14:29:29
- Link: https://github.com/clev1l/2025/02/23/reversing-kr-WP/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments