DASCTF 2024暑期挑战赛WP

DosSnake
瞪眼一个异或
1 | enc=[0x3F, 0x09, 0x63, 0x34, 0x32, 0x13, 0x2A, 0x2F, 0x2A, 0x37, |
DASCTF{H0wfUnnytheDosSnakeis!!!}
Strangeprograme
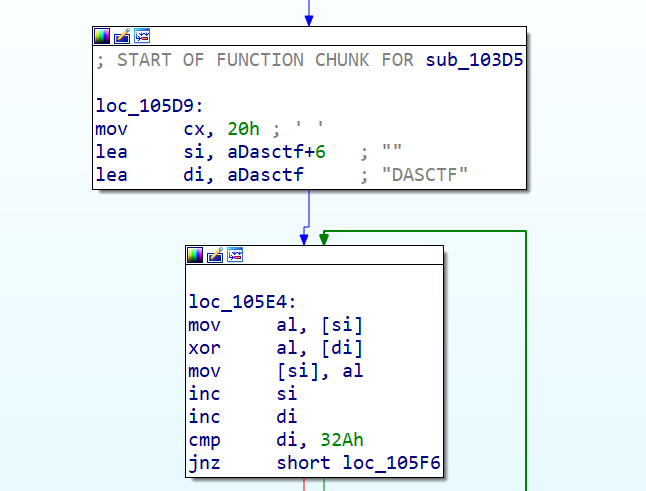
找到DASCTF段,往上跟
先是smc解密DASCTF段代码,然后注册hook
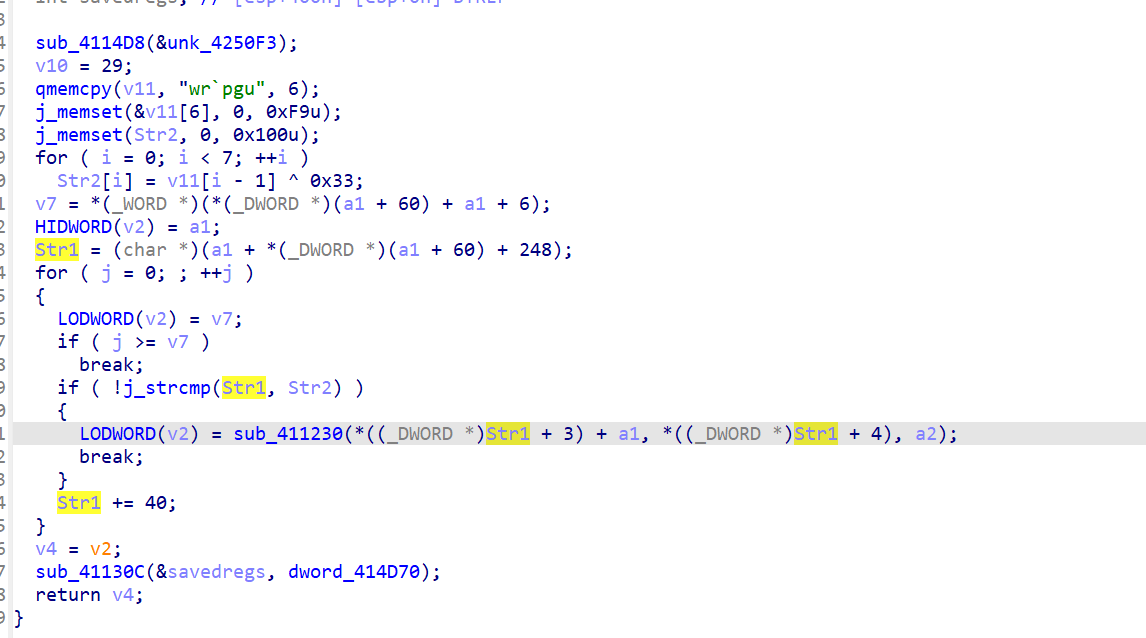
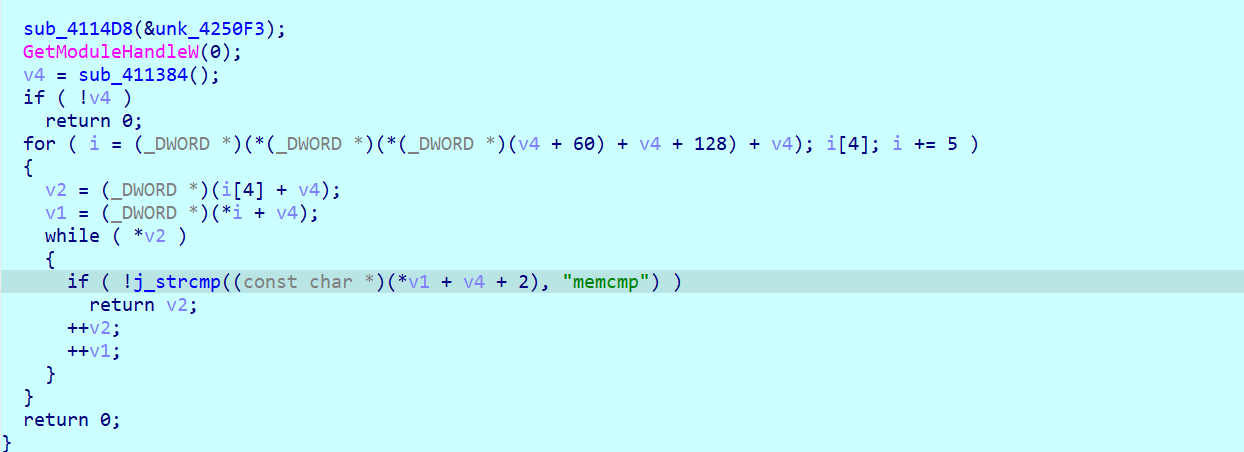
绕反调试
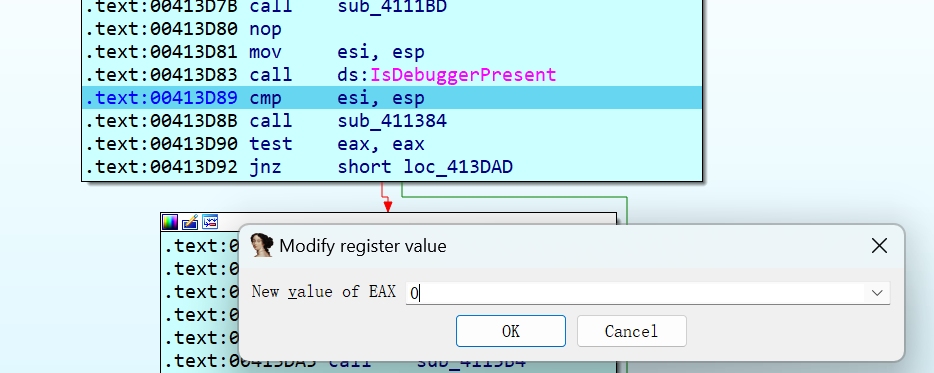
输入后打硬件断点跟到关键代码,魔改tea,照着解密就行
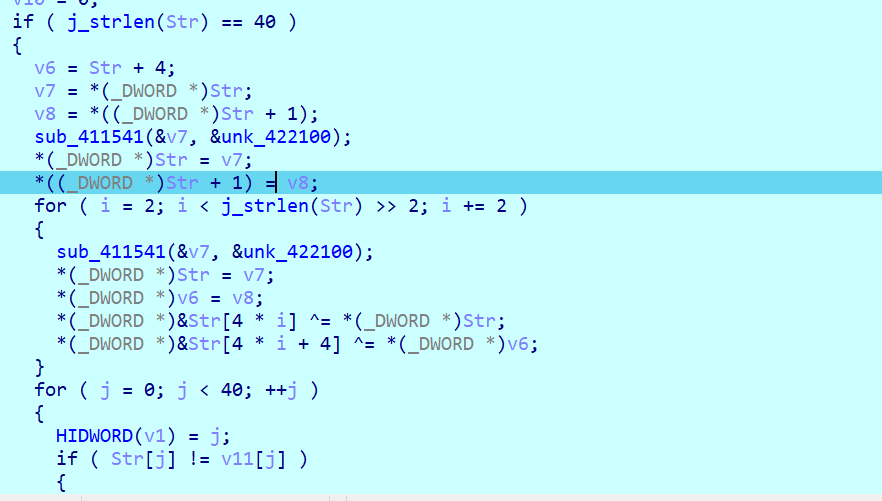
1 | from ctypes import * |
DASCTF{I4TH0ok_I5S0ooFunny_Isnotit?????}
BabyAndroid
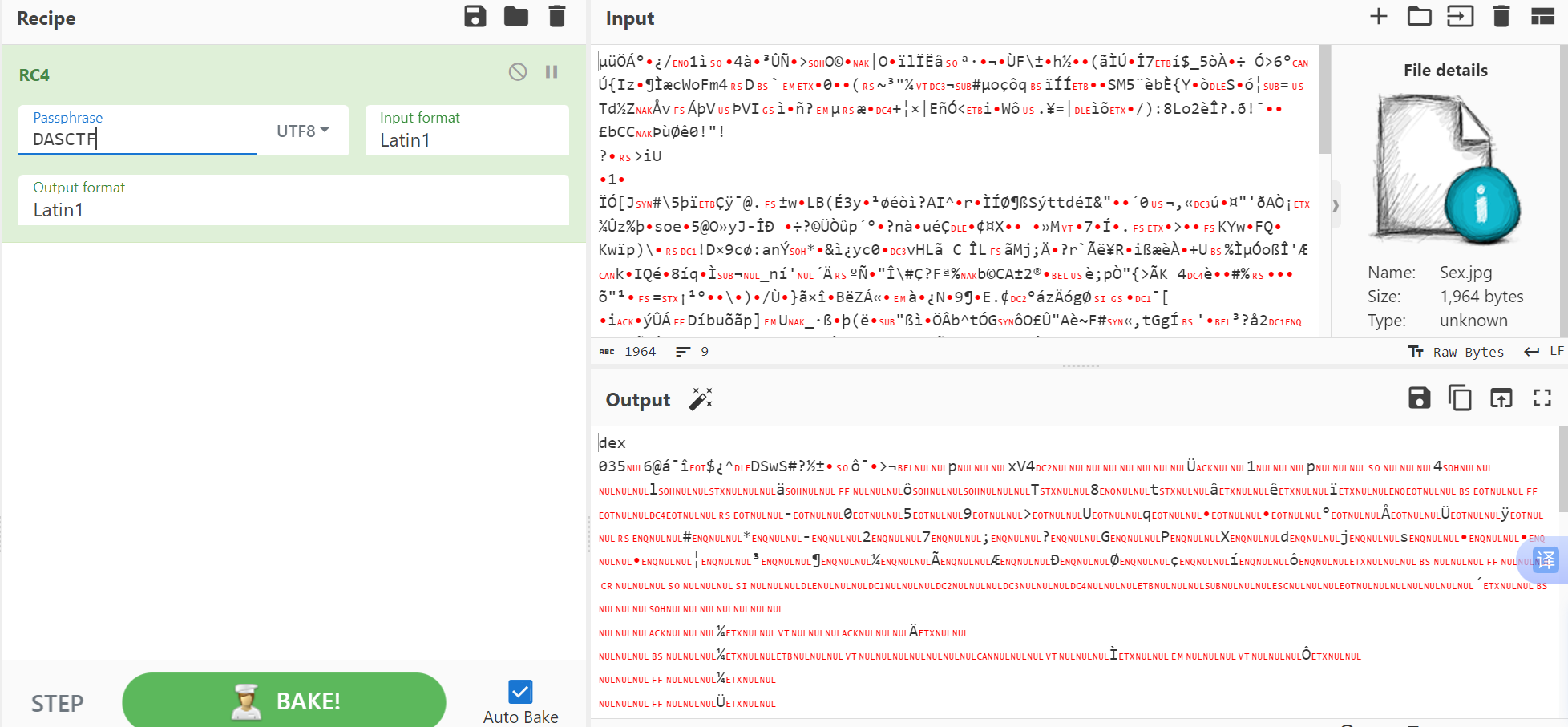
资源文件找到一个Sex.jpg,直接搜
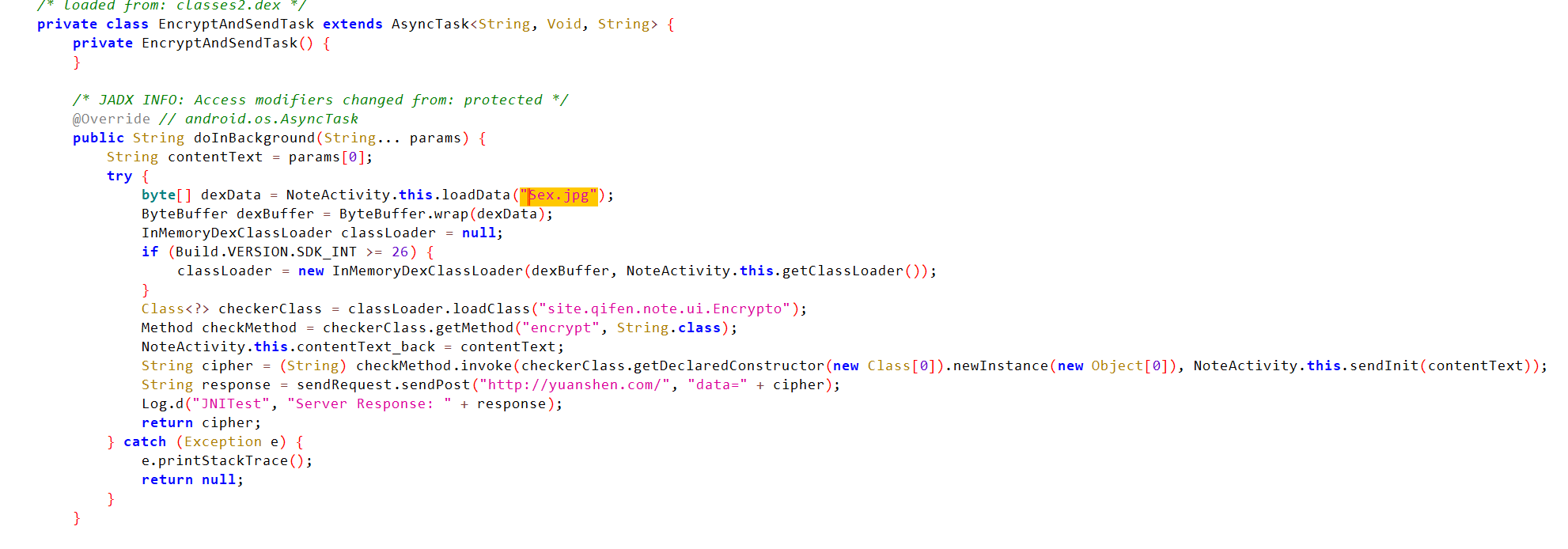
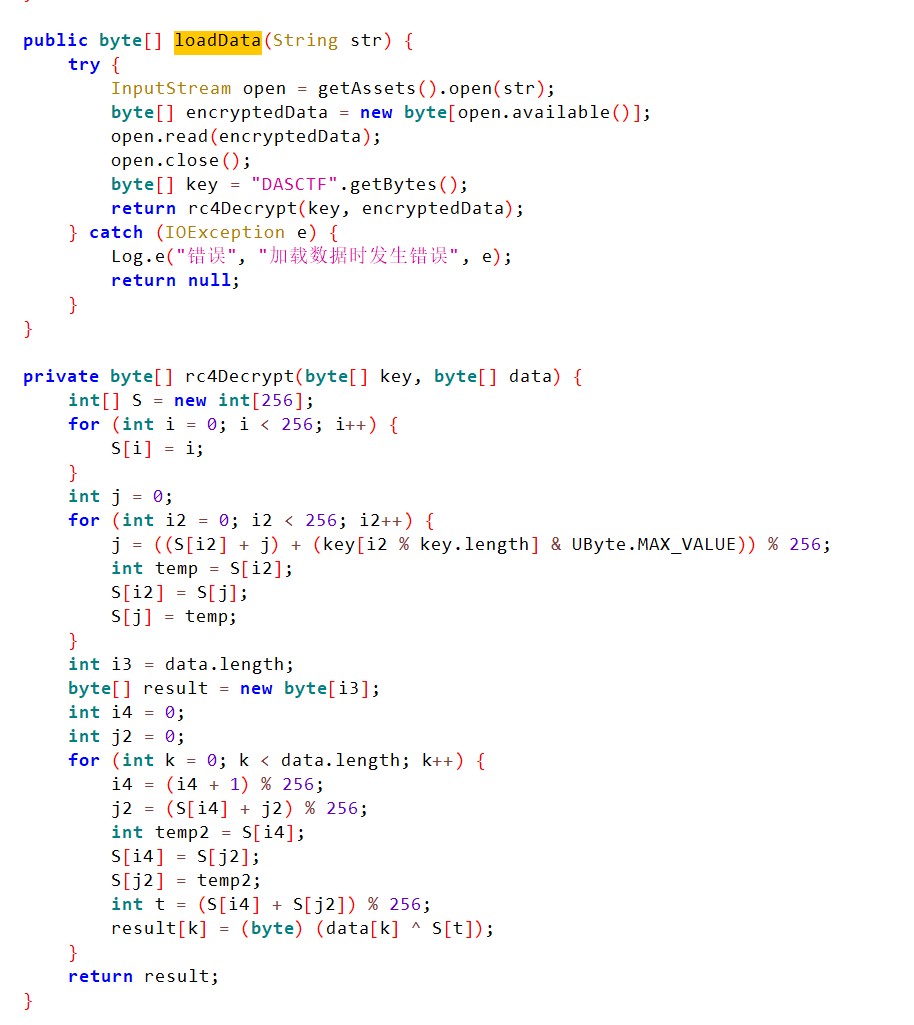
动态加载类,先用rc4解密一下
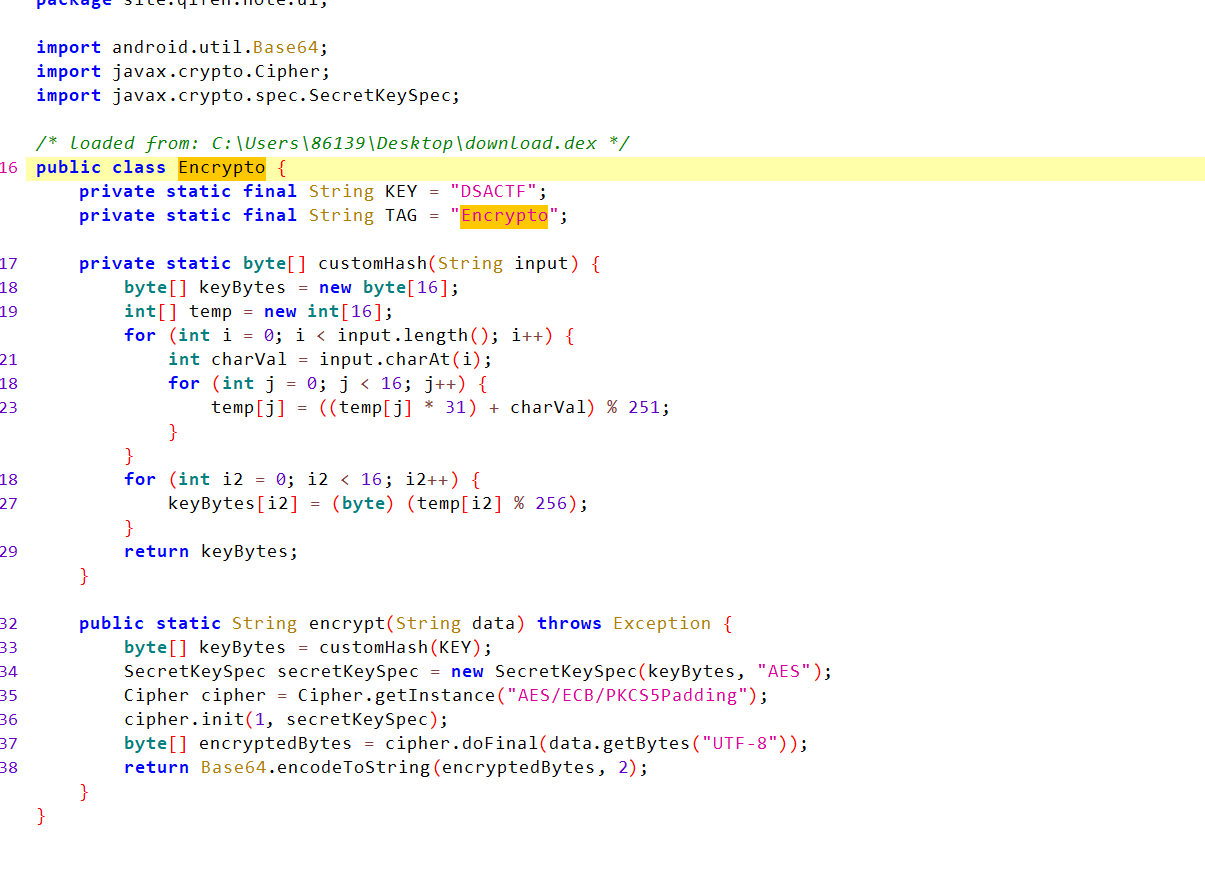
aes+base64
1 | import java.nio.charset.StandardCharsets; |
代码中还调用了sendInit,在native层
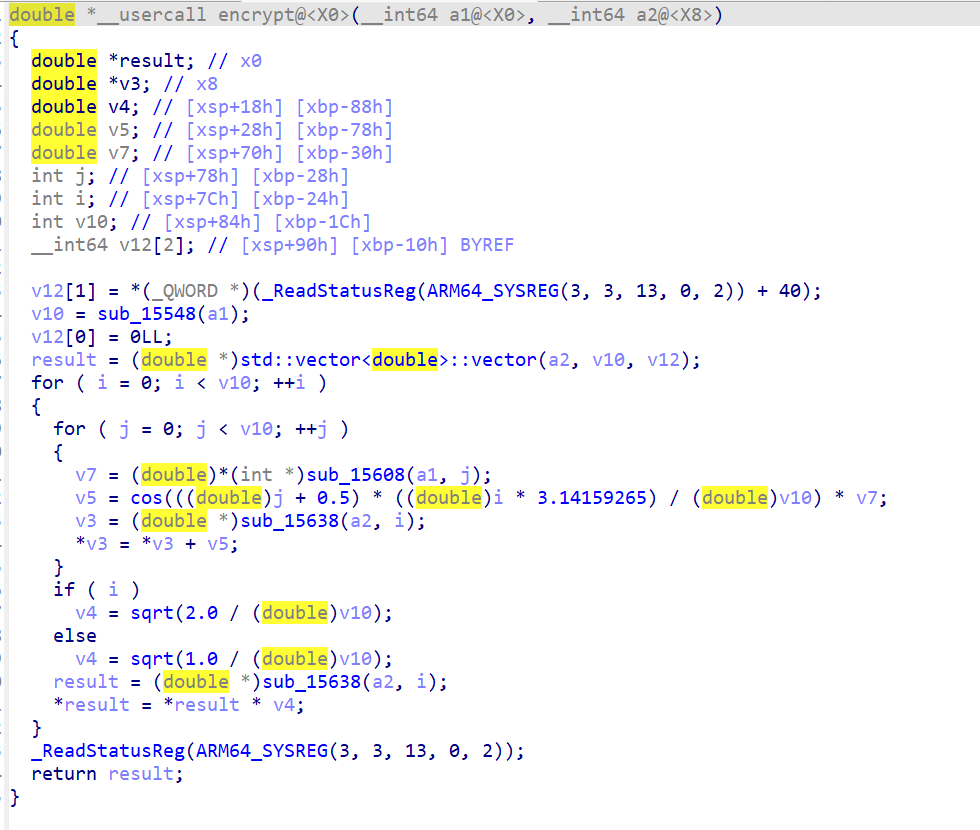
扔给gpt秒了
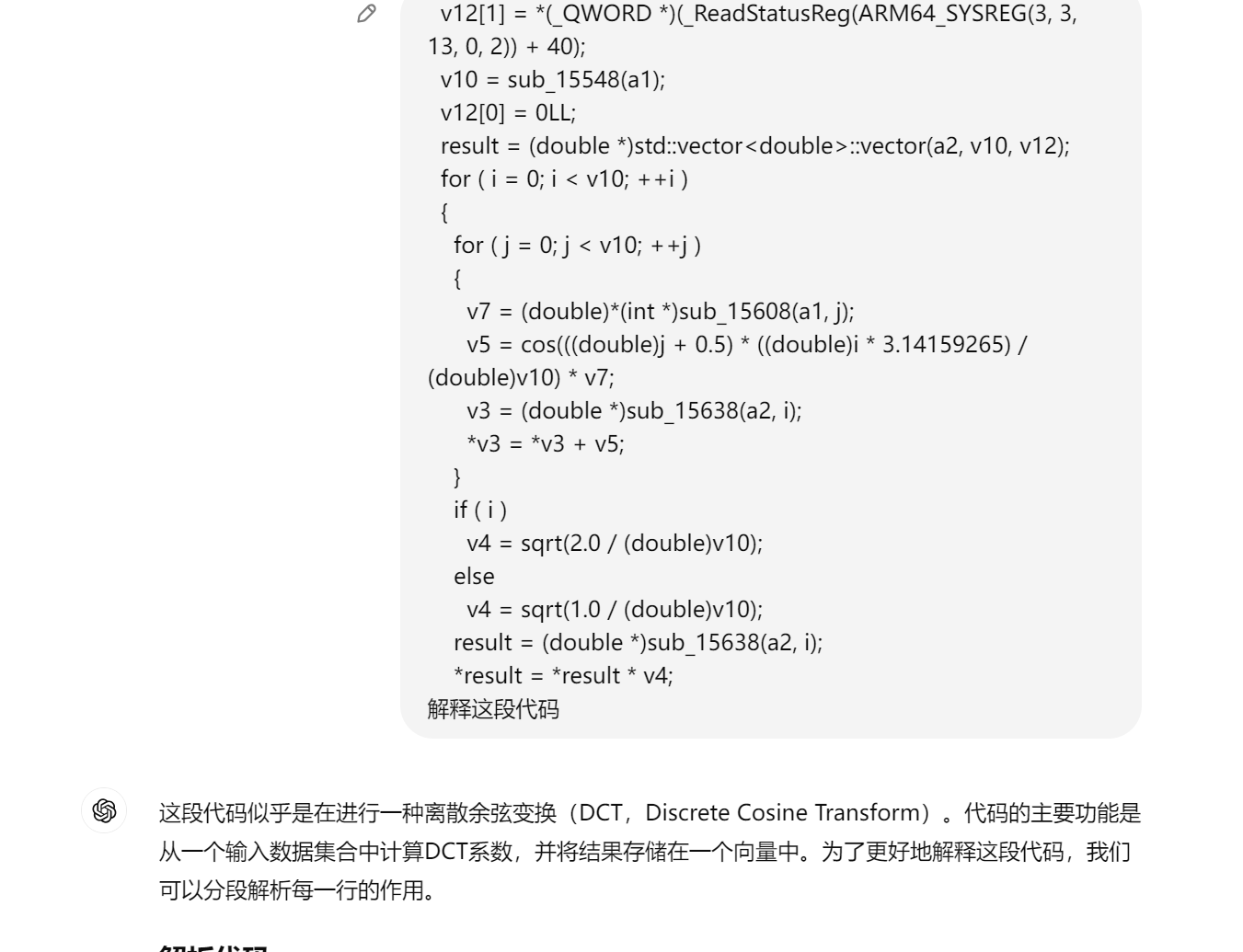
1 | import numpy as np |
DASCTF{Y0u_Ar3Re4lly_H@ck3r!}
- Title: DASCTF 2024暑期挑战赛WP
- Author: clev1L
- Created at : 2024-07-20 12:50:36
- Updated at : 2025-04-07 14:29:29
- Link: https://github.com/clev1l/2024/07/20/DASCTF-2024暑期挑战赛WP/
- License: This work is licensed under CC BY-NC-SA 4.0.
Comments